In order to configure Clustered JMX, use the following command line parameters for your Management Center deployment.
-
-Dhazelcast.mc.jmx.enabled=true(default is false) -
-Dhazelcast.mc.jmx.port=9000(optional, default is 9999) -
-Dcom.sun.management.jmxremote.ssl=false -
-Dhazelcast.mc.jmx.rmi.port=9001(optional, default is 9998) -
-Dhazelcast.mc.jmx.host=localhost(optional, default is server’s host name)
With embedded Jetty, you do not need to deploy your Management Center application to any container or application server.
You can start the Management Center application with Clustered JMX enabled as shown below.
java -Dhazelcast.mc.jmx.enabled=true
-Dhazelcast.mc.jmx.port=9999
-Dcom.sun.management.jmxremote.ssl=false -jar hazelcast-management-center-4.2021.12.jarOnce the Management Center starts, you should see a log similar to the one below:
INFO: Management Center 3.3
Jun 05, 2014 11:55:32 AM com.hazelcast.webmonitor.service.jmx.impl.JMXService
INFO: Starting Management Center JMX Service on port :9999You should be able to connect to the Clustered JMX interface
using the address localhost:9999.
You can use jconsole or any other JMX client to monitor your
Hazelcast IMDG cluster. As an example, below is the jconsole
screenshot of the Clustered JMX hierarchy.
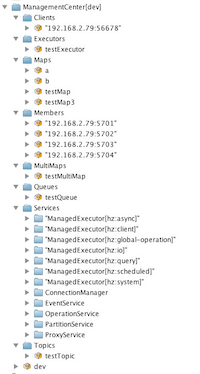
Enabling TLS/SSL for Clustered JMX
By default, Clustered JMX is served unencrypted. To enable TLS/SSL for Clustered JMX, use the following command line parameters for your Management Center deployment:
-
-Dhazelcast.mc.jmx.ssl=true(default is false) -
-Dhazelcast.mc.jmx.ssl.keyStore=path to your keystore -
-Dhazelcast.mc.jmx.ssl.keyStorePassword=password for your keystore
The following is an example on how to start the Management Center with a TLS/SSL enabled Clustered JMX service on port 65432:
java -Dhazelcast.mc.jmx.enabled=true
-Dhazelcast.mc.jmx.port=65432
-Dhazelcast.mc.jmx.ssl=true
-Dhazelcast.mc.jmx.ssl.keyStore=/some/dir/selfsigned.jks
-Dhazelcast.mc.jmx.ssl.keyStorePassword=yourpassword
-jar hazelcast-management-center-4.2021.12.jar| You can encrypt the keystore password and pass it as a command line argument in encrypted form for improved security. See the Variable Replacers section for more information. |
Then, you can use the following command to connect to the
Clustered JMX service using JConsole with the address localhost:65432:
jconsole -J-Djavax.net.ssl.trustStore=/some/dir/selftrusted.ts -J-Djavax.net.ssl.trustStorePassword=trustpassEnabling TLS Mutual Authentication for Clustered JMX
In order to secure the Clustered JMX interface, you can use the following command line parameters to enable TLS mutual authentication:
-
-Dhazelcast.mc.jmx.mutualAuthentication=true(default is false) -
-Dhazelcast.mc.jmx.ssl.trustStore=path to your truststore -
-Dhazelcast.mc.jmx.ssl.trustStorePassword=password for your truststore
The following is an example on how to start Management Center with a TLS mutual authentication enabled Clustered JMX service on port 65432:
java -Dhazelcast.mc.jmx.enabled=true
-Dhazelcast.mc.jmx.port=65432
-Dhazelcast.mc.jmx.ssl=true
-Dhazelcast.mc.jmx.mutualAuthentication=true
-Dhazelcast.mc.jmx.ssl.keyStore=/some/dir/selfsigned.jks
-Dhazelcast.mc.jmx.ssl.keyStorePassword=yourpassword
-Dhazelcast.mc.jmx.ssl.trustStore=/some/dir/truststore.jks
-Dhazelcast.mc.jmx.ssl.trustStorePassword=yourpassword
-jar hazelcast-management-center-{page-component-version}.jarAdditional TLS/SSL Configuration Options
The following are some additional command line arguments that you can use to configure TLS/SSL for clustered JMX:
-
-Dhazelcast.mc.jmx.ssl.keyStoreType: Type of the keystore. Its default value is JKS. -
-Dhazelcast.mc.jmx.ssl.keyManagerAlgorithm: Name of the algorithm based on which the authentication keys are provided. The system default is used if none is provided. You can find out the default by calling thejavax.net.ssl.KeyManagerFactory#getDefaultAlgorithmmethod.
